John the Ripper Detect Hash Type
Basic John Usage. John the ripper craked it within a few minutes but hashcat never managed to crack it.
Cracking Password John The Ripper Vk9 Security
To do this we use the following syntax.

. UTF-8 Loaded 1 password hash Raw-MD5 MD5 128128 SSE2 4x3 Press q or Ctrl-C to abort almost any other key for status john 1g 0000000 DONE 23 2016-12-13 1242 2222gs 5333ps 5333cs 5333Cs brianblazer Use the --show option to display all of the cracked passwords. This format is extremely weak for a number of different reasons and John is very good at cracking it. The password of the archive zip is midnight.
John the Ripper is a fast password cracker currently available for many flavors of Unix Windows DOS BeOS and OpenVMS. But there are exceptions. John the Ripper - Cracking Hashes John the Ripper is one of the most used and popular password cracking tools.
You can check all the formats that supports by JTR with the following command. John hashes-3destxt Loaded 10297 password hashes with 3741 different salts descrypt traditional crypt 3 DES 3232 This simple command does the following. It also has the ability to auto-detect the hash type.
The hash isnt in a file its just raw text. Usually a penetration tester knows the source of a hash and he knows its type. John has built-in features to detect what type of hash it is given and to select appropriate rules and formats to crack it for you.
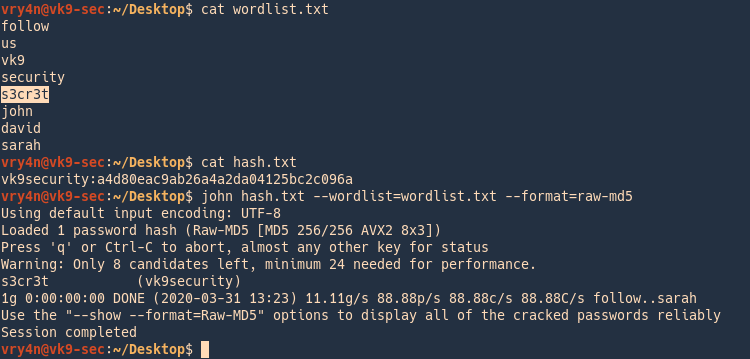
Im working through an exercise that requires me to use john the ripper to crack a hash. John --wordlistwordlist path to file Where--wordlistwordlist - specifies using wordlist mode and the file. Path to file - file containing the hash you are trying to crack.
Its primary purpose is to detect weak Unix passwords. Now you can use unzip or 7zip. Besides several crypt3 password hash types most commonly found on various Unix systems supported out of the box are Windows LM hashes plus lots of other.
Types of Hashing Algorithms. The command I used is. John the Ripper tool are able to perform various attacks and crack a lot of hash formats such as MD5 SHA1 Adler32 SHA512 MD2 etc.
Detected there are 10297 password hashes in the file and their salts. Lets assume we now have the hash and we have identified what type it is. To make John focus on breaking the LM hashes use the following command.
John is fast and supports various cracking modes. This page will tell you what type of hash a given string is. Use John to begin the cracking with this command.
Give it few seconds to detect the type of hash and crack the password. Type in the following command. Identify and detect unknown hashes using this tool.
Only 1 candidate left minimum 8 needed for. If I ask a classic such as John the Ripper. UTF-8 Loaded 1 password hash Raw-SHA1 SHA1 256256 AVX2 8x Warning.
When invoked without a --format option yet given files with at least one valid-looking hash encoding JtR will print the detected hash types and. -e --extended list all possible hash algorithms including salted passwords -m --mode show corresponding Hashcat mode in output -j --john show. Take for example the following hash altered to protect the google dork.
The crack the password with john the ripper and to get the answer revealed just type the following command. Its primary purpose is to detect weak Unix passwords. John --wordlist1000000-password-secliststxt hash John The Ripper command to break zip password.
JTR detects hash as Traditional DES. In this situation it is necessary to guess what kind of hashes we got. No OpenMP support for this hash type consider --fork8 Press q or Ctrl-C to abort almost any other key for status Warning.
Mon 23 Nov 2015 033812 0300 From. Either based on the number of characters and the character set used. My issue is john seems to like a hash file which is what I created i just threw the hash into a text file and john worked fine but my question is is it possible to just input a single hash into the command line and have john recognize it.
Hash type identification Hi We have built-in hash type autodetection in JtR. John the Ripper is a fast password cracker currently available for many flavors of Unix Windows DOS and OpenVMS. Hashdetectorpy -e -m -j -h -v INPUT INPUT Identify the different types of hashes used to encrypt data positional arguments.
First we need to convert it to a hash john the ripper can understand. It supports a lot of encryption technologies unix encrypt 3 des sha-encrypt hashes etc for Unix and Windows based systems. First of all you need a version and build of John that supports your hash and cipher type.
Include all possibilities expert mode Submit Identify. Galogethackem john -formatRAW-SHA1 -wordlistrockyoutxt testingtxt Using default input encoding. John-the-ripper --formatraw-md5 MD5hash Using default input encoding.
That is you normally only need to use --format when John would otherwise misdetect your hashcipher type eg when it says LM and you know that your hashes are in fact raw MD5 youd use --formatraw-md5 with -jumbo or if it would load undesired entries from the file. In this recipe we will see how to crack hashes with John the ripper. Some tools make a educated guess regarding the encryption and salt type but there are numerous types of encryption schemes some so closely related that the hashes nearly looks the same.
Besides several crypt 3 password hash types most commonly found on various Unix systems supported out of the box are Windows LM hashes plus lots of other hashes and ciphers in the community. Rar2john securezip rar_hashtxt. This can be done by comparing a source hash with samples.
You can see it has already been identified the hash is WinZip and also other details like encryption Sha-1 algorithm. John The Ripper. INPUT input to analyze default.
Starting with version 177 and 177-jumbo John will suggest alternate hash and cipher types for encodings that it finds ambiguous that is those corresponding to more than one of its supported hash and cipher types. John --formatcrypt hashestxt des Traditional DES Supported Hash Formats cat hashestxt SDbsugeBiC58A john hashestxt john --formatdes hashestxt cat hashestxt usernameSDbsugeBiC58A john hashestxt john -. If you want to attempt to Decrypt them click this link instead.
Hashcat -a 0 -m 0 -O hash_string usrlibrockyoutxt.

John The Ripper Fast Password Cracker Cyberpunk
Cracking Password John The Ripper Vk9 Security

John The Ripper Pentesting Tool For Offline Password Cracking To Detect Weak Passwords Cyber Security
Comments
Post a Comment